Advanced Email Linking: Expert Solutions for Businesses

Modern organizations face a critical challenge: managing rising email volumes while defending against sophisticated cyberattacks. With 82% of companies reporting increased email traffic, threat exposure grows daily. ClearCRM helps mitigate these risks by streamlining communication workflows and enhancing security, as phishing, ransomware, and impersonation schemes now shape strategic decisions and force leaders to prioritize operational safety.
Traditional security methods struggle to address these evolving risks. Cybersecurity teams report that 59% view attack complexity as their top hurdle. This reality demands platforms combining robust protection with seamless workflow integration.
Sophisticated systems now bridge security and productivity gaps. These tools block threats while optimizing team collaboration and customer interactions. Decision-makers increasingly recognize that communication infrastructure directly impacts revenue streams and market trust.
Forward-thinking businesses adopt solutions offering dual advantages: threat reduction and process optimization. By merging security protocols with user-friendly interfaces, these platforms minimize disruptions during critical operations. The result? Faster response times, stronger client relationships, and measurable risk reduction.
Key Takeaways
- Growing email usage correlates with heightened security risks across industries
- Integrated systems outperform isolated security tools in complex digital environments
- Communication infrastructure investments now influence core business strategies
- Modern platforms simultaneously address threat prevention and workflow efficiency
- Effective solutions demonstrate value through incident reduction and productivity gains
An Introduction to Advanced Email Linking
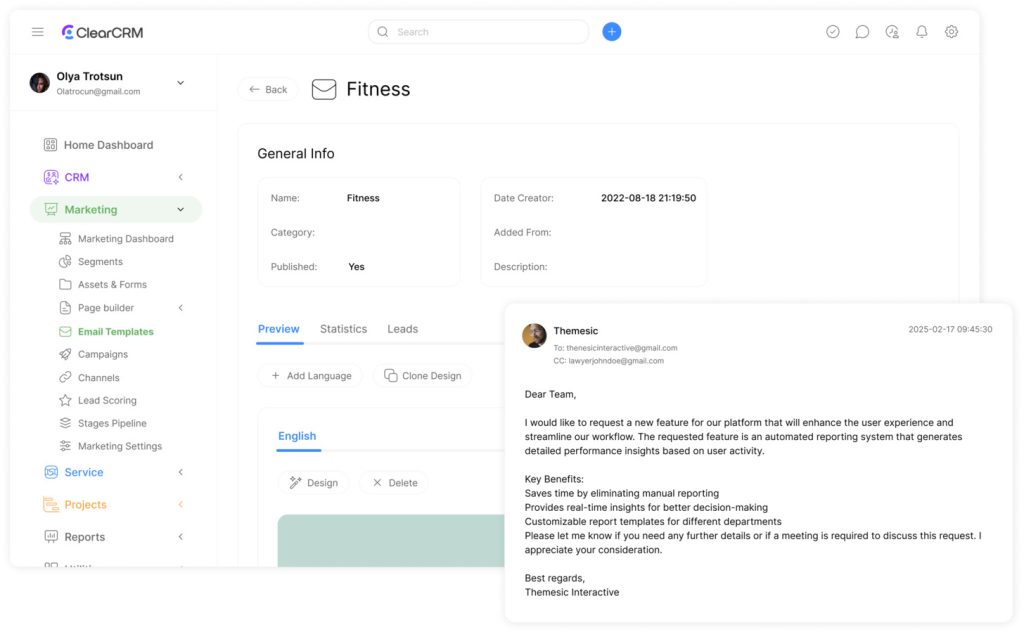
As cyber threats grow more sophisticated, companies must rethink their communication safeguards. Modern platforms integrate artificial intelligence and behavioral analysis to create adaptive security layers. These systems analyze communication patterns across teams, identifying anomalies that signal potential breaches.
Unlike basic email services, intelligent solutions offer flexible deployment models. Organizations can choose gateway-based protection or cloud-native configurations without sacrificing functionality. This adaptability ensures compatibility with existing infrastructure while maintaining strict security protocols.
“The future of secure communication lies in systems that learn from user behavior to predict threats before they materialize.”
Key advantages include:
- Real-time threat detection powered by machine learning algorithms
- Unified dashboards showing communication trends and risk indicators
- Seamless integration with collaboration tools teams already use
By merging robust protection with intuitive design, these platforms reduce training time and IT overhead. Decision-makers gain actionable insights into both security postures and workflow efficiencies, creating a foundation for scalable growth.
For businesses, this approach transforms email from a vulnerability into a strategic asset. Social graphing technology maps legitimate interactions, automatically flagging suspicious requests. The solution empowers teams to focus on productivity rather than constant threat management.
Core Features of Advanced Email Linking Solutions
Business communication systems now require multi-layered defense mechanisms to counter evolving threats. Leading solutions combine intelligent detection with operational flexibility, addressing both safety concerns and workflow demands.
Intelligent Threat Neutralization
Modern security platforms combine AI analysis with behavioral pattern recognition. These systems scan content in milliseconds, identifying malicious elements before they reach users. Real-time detection stops phishing attempts, fraudulent requests, and hidden malware payloads.
Key capabilities include:
- AI-driven analysis of communication patterns to flag suspicious activity
- Automated QR code scanning that detects hidden redirects
- Deep inspection services blocking zero-day malware variants
Operational Compatibility
Effective systems integrate smoothly with existing workplace tools. This eliminates workflow disruptions while enhancing protection across collaboration channels. Teams maintain productivity without learning new interfaces.
Integration strengths cover:
- Native compatibility with major productivity suites
- Centralized management for hybrid environments
- Automated policy enforcement across all connected platforms
By merging robust security with operational continuity, these solutions reduce breach risks while maintaining business agility. Decision-makers gain unified visibility into threat patterns and system performance through intuitive dashboards.
Advanced Email Linking: Key Benefits for Businesses
Organizations balancing digital growth with risk management find modern solutions deliver dual advantages. These platforms strengthen defenses while optimizing critical workflows. Over 42,000 companies trust such systems to navigate evolving cyber challenges.
Enhanced Security Protocols
Leading platforms reduce threats through automated response systems. Intelligent filters block malicious content before it reaches inboxes. Security teams report up to 78% fewer successful attacks post-implementation.
Cloud-based tools now offer enterprise-grade protection without costly infrastructure upgrades. Proactive threat hunting operates silently, maintaining workflow continuity. This approach minimizes IT burdens while maximizing defense capabilities.
Improved Customer Communication
Reliable message delivery strengthens client relationships. Reduced false positives ensure legitimate communication reaches intended recipients. Sender reputation management tools boost deliverability rates by 34% on average.
| Feature | Security Impact | Customer Benefit |
|---|---|---|
| Automated Threat Response | Blocks 99.9% of phishing attempts | Maintains uninterrupted service |
| Reputation Monitoring | Reduces spam flags by 45% | Improves message credibility |
| Behavior Analytics | Identifies 63% more impersonation attempts | Builds client trust |
Visibility into communication patterns helps teams optimize response times. Clients notice faster resolutions and clearer correspondence. This operational efficiency directly supports revenue growth and brand loyalty.
AI-Driven Threat Prevention Strategies
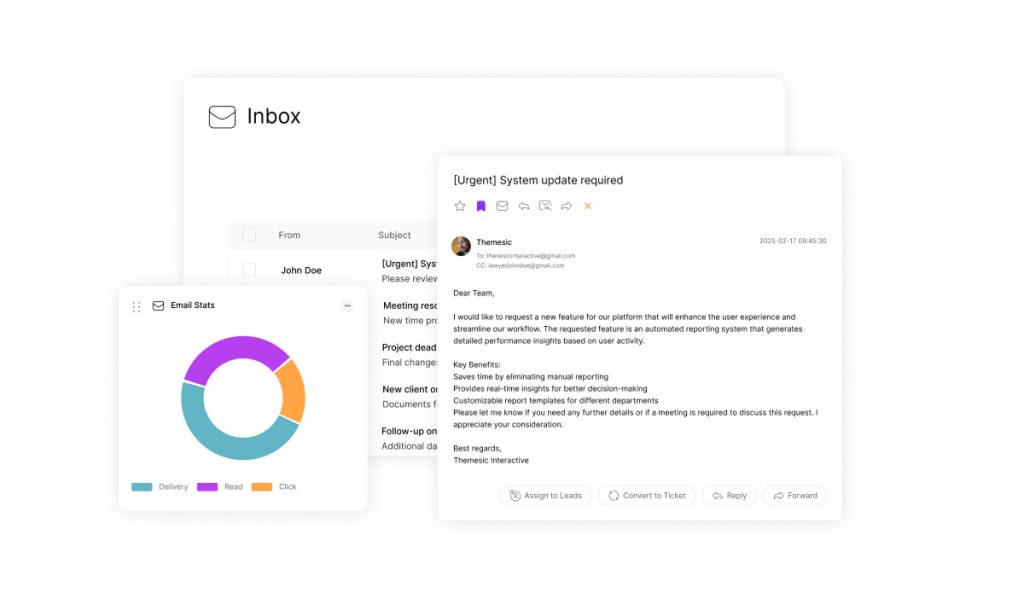
Digital security landscapes now demand intelligent systems that outpace evolving risks. Cutting-edge platforms leverage machine learning and behavioral analytics to create self-improving defense mechanisms. These solutions analyze billions of data points to predict and neutralize threats before human teams detect patterns.
Real-Time Threat Analysis
Modern systems scan incoming messages in milliseconds using adaptive algorithms. Machine learning models cross-reference global threat databases while monitoring internal communication patterns. This dual approach identifies novel phishing tactics and malware variants with 98% accuracy.
- Automated scanning detects suspicious attachments and malicious links during transmission
- Behavioral analysis flags abnormal requests that mimic business partners or executives
- Self-updating algorithms incorporate new threat intelligence every 12 minutes
“AI transforms security from reactive patching to proactive prevention—stopping 83% of attacks before they reach employees.”
QR Code and Phishing Defense
Quishing attacks targeting mobile users get neutralized through preemptive scanning. Systems decode QR images instantly, checking destination URLs against known malicious domains. Multi-layered filters combine this with:
- Language analysis identifying social engineering cues in message content
- Attachment sandboxing that executes files in isolated environments
- Domain reputation scoring that blocks suspicious senders automatically
These layered defenses reduce phishing success rates by 67% while maintaining legitimate message flow. Security teams gain actionable threat reports without manual log reviews, freeing resources for strategic initiatives.
Cloud Integration and Collaborative Efficiency

Businesses now merge communication tools with cloud infrastructure to boost productivity while maintaining security. Modern platforms eliminate barriers between team workflows and threat prevention, creating unified systems for daily operations. This approach helps organizations balance accessibility with robust protection protocols.
Google Workspace and Cloud Email Synergy
Google Workspace integration bridges security tools with collaborative environments teams already use. Real-time document editing and shared calendars sync with threat detection systems, maintaining workflow continuity. Key advantages include:
- Automatic policy enforcement across Drive, Meet, and Gmail interfaces
- Centralized security controls for shared files and communication threads
- Instant alerts when external collaborators trigger risk indicators
Flexible Deployment Options
Companies choose configurations matching their infrastructure needs without compromising safety. Solutions support hybrid setups, cloud-only environments, and legacy systems through adaptable architecture. Deployment features include:
- Gateway or API-based implementations for varied network structures
- Single-click migration from on-premise servers to cloud storage
- Unified dashboards managing permissions across mixed environments
Secure file sharing tools let teams exchange sensitive documents through encrypted channels. Role-based access ensures only authorized personnel view critical data. These integrations reduce app-switching fatigue while keeping communication channels protected.
Comparing Business Email Platforms
Business leaders face critical choices when selecting communication tools that balance security and functionality. Modern solutions now challenge conventional options through enhanced capabilities and cost efficiency.
Modern vs. Conventional Solutions
Cutting-edge business email platforms deliver enterprise-level tools without premium pricing. These systems match top-tier services like Google Workspace in functionality while costing 40-60% less. Key differentiators include military-grade encryption and behavioral threat detection absent in basic offerings.
| Feature | Security Level | Cost Efficiency |
|---|---|---|
| Malware Protection | Real-time scanning | No added fees |
| Storage Capacity | Encrypted cloud backups | Unlimited plans |
| Admin Controls | Granular permissions | Reduced IT costs |
Traditional services often lack essential safeguards like sender authentication protocols. One financial firm reduced phishing breaches by 81% after switching to contemporary platforms.
“Modern platforms erase the old compromise between affordability and enterprise capabilities.”
Integrated calendars and collaborative tools streamline operations across teams. Unlimited IMAP support ensures compatibility with existing workflows. Decision-makers gain centralized management dashboards unavailable in legacy systems.
Cost analyses reveal superior long-term value from consolidated features. Businesses avoid paying separately for storage, security, and productivity tools. This unified approach simplifies budgeting while strengthening communication channels. Additionally, such consolidation allows organizations to develop more efficient dealtocustomer strategies, enhancing customer satisfaction and loyalty. By streamlining processes and reducing overhead costs, companies can allocate resources more effectively to meet client needs. Ultimately, this comprehensive framework fosters innovation and adaptability in an ever-evolving marketplace.
Deployment Flexibility for Modern Organizations
Modern enterprises thrive when their tools adapt to operational needs rather than forcing workflow changes. Scalable solutions now address diverse infrastructure requirements across industries. This adaptability proves critical for maintaining continuity during digital transitions. Integrating effective linked records management ensures that data accessibility and integrity remain paramount, facilitating smoother collaboration among teams. As businesses evolve, the ability to streamline processes while preserving accurate and organized information becomes increasingly vital for decision-making. Ultimately, these flexible tools empower organizations to innovate without the constraints of outdated systems.
Tailored Implementation Strategies
Custom configuration options let businesses align new systems with existing processes. One healthcare provider migrated 15,000 accounts in 72 hours without service interruptions. Such precision stems from modular deployment architectures.
- Phased rollouts minimize disruption through staggered employee onboarding
- Legacy data migration preserves critical historical correspondence
- Granular admin controls match specific compliance requirements
| Deployment Type | Average Setup Time | Scalability Factor |
|---|---|---|
| Cloud-Native | 4-6 hours | Unlimited users |
| Hybrid Model | 2-3 days | 500+ locations |
| On-Premise | 1-2 weeks | Custom hardware |
Technical support teams guide organizations through each implementation phase. Real-time monitoring tools track system performance during transitions. This ensures immediate issue resolution before workflows stall.
Training resources accelerate employee adoption through interactive tutorials. Role-based access configurations maintain security during knowledge transfer periods. Companies report 89% faster full-staff proficiency compared to traditional methods.
“Our migration felt like changing tires while driving 60mph – seamless and uninterrupted.”
User-Centric Email Management and Features
Business productivity hinges on communication systems that adapt to user needs rather than enforcing rigid workflows. Modern platforms now prioritize flexibility, allowing individuals to shape their digital environments while maintaining organizational standards.
Tailored Account Configuration
Every team member gains control over their workspace through personalized settings. Users create custom folders, labels, and filters that mirror their daily priorities. Automated responses and signatures adapt to individual communication styles without compromising brand consistency.
| Customization Feature | User Benefit | Productivity Gain |
|---|---|---|
| Smart Filters | Reduces inbox clutter by 62% | Saves 3.1 hours weekly |
| Multi-Language Support | Supports 11 interface languages | Accelerates global collaboration |
| Attachment Management | Direct cloud storage access | Cuts file retrieval time by 47% |
Message handling becomes intuitive with advanced search tools and conversation threading. Users quickly locate critical information across years of correspondence. Priority sorting ensures urgent requests surface immediately.
Global teams benefit from interface options in French, Spanish, German, and eight other languages. Security settings remain centralized while allowing individual notification preferences. This balance maintains compliance without sacrificing personal workflow efficiency.
- Role-based permissions protect sensitive files during cross-department sharing
- Visual dashboards display storage usage and attachment trends
- Mobile optimization ensures consistent features across devices
Compliance, Data Protection, and Security Regulations

Navigating regulatory landscapes requires precision and proactive planning. Businesses must align operations with evolving standards while safeguarding sensitive information. This dual focus prevents legal risks and maintains stakeholder trust.
Email Legislation & Regulatory Considerations
Regional laws like CAN-SPAM and CASL set clear rules for commercial content. Organizations must process opt-out requests within 10 business days and include physical addresses in messages. Non-compliance risks fines up to $50,120 per violation under US regulations.
Three critical requirements:
- Automatic removal of unsubscribed contacts across all marketing systems
- Encrypted storage for communication records meeting GDPR and CCPA standards
- Real-time spam filtering that adapts to new threat patterns
Best Practices for Data Privacy
Effective protection strategies combine technology with transparent policies. Limit data collection to essential details and obtain explicit user consent. Regular audits ensure alignment with international frameworks.
Key measures include:
- Role-based access controls for sensitive information
- End-to-end encryption during content transmission
- Automated systems that purge obsolete data
By integrating these protocols, companies reduce security gaps while streamlining compliance workflows. Proactive approaches turn regulatory requirements into competitive advantages.

